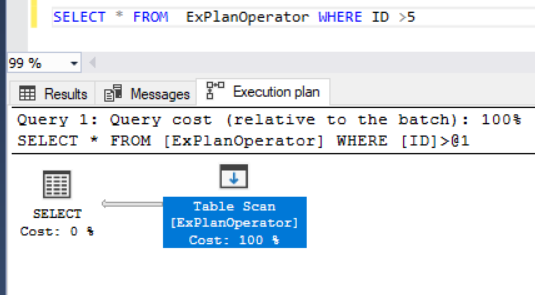
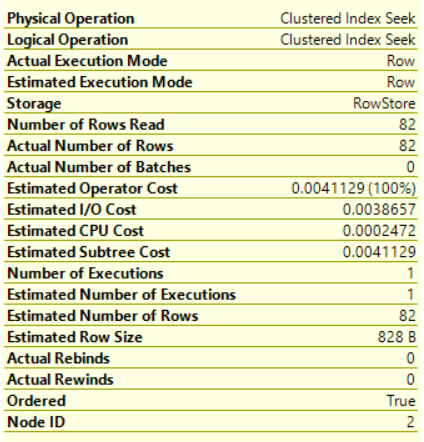
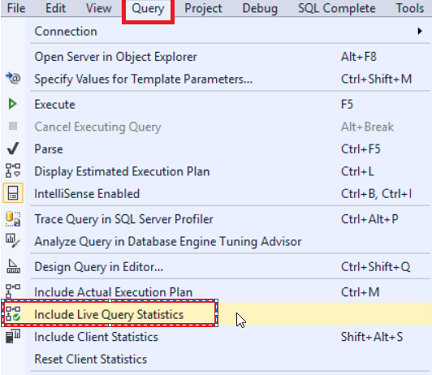
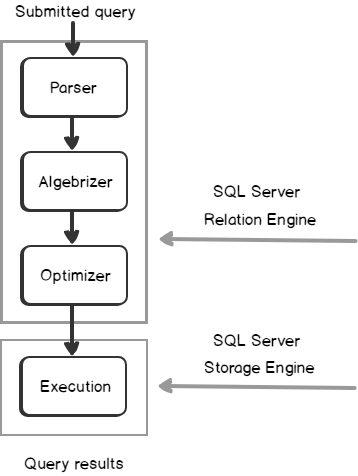
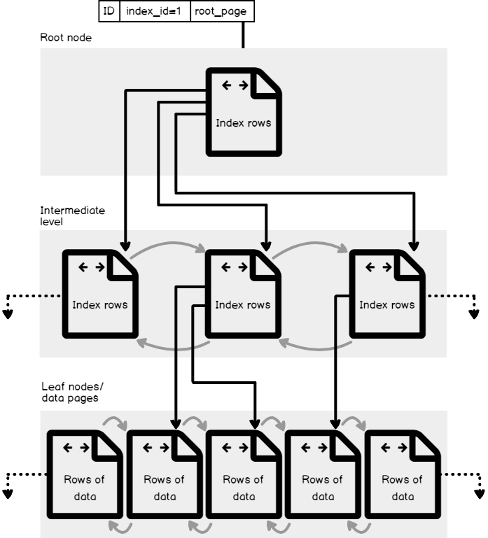
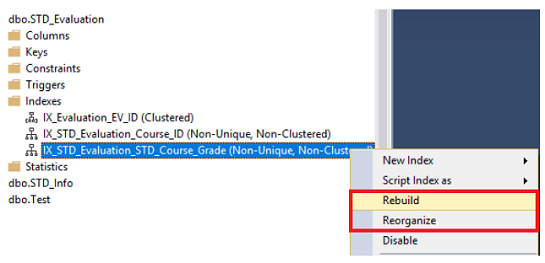
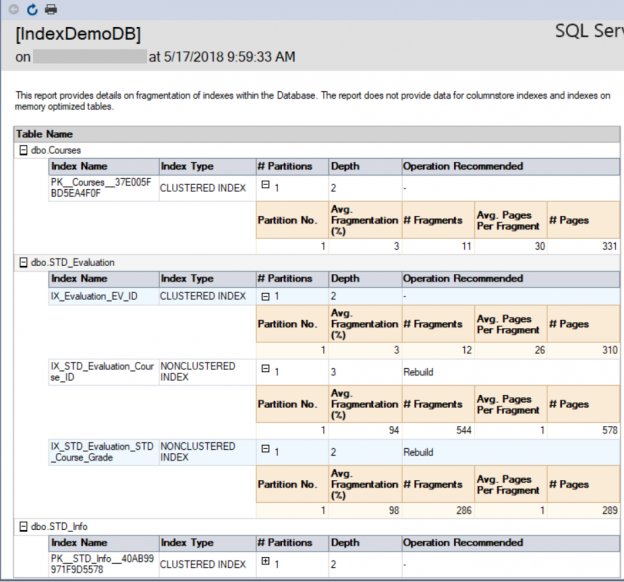
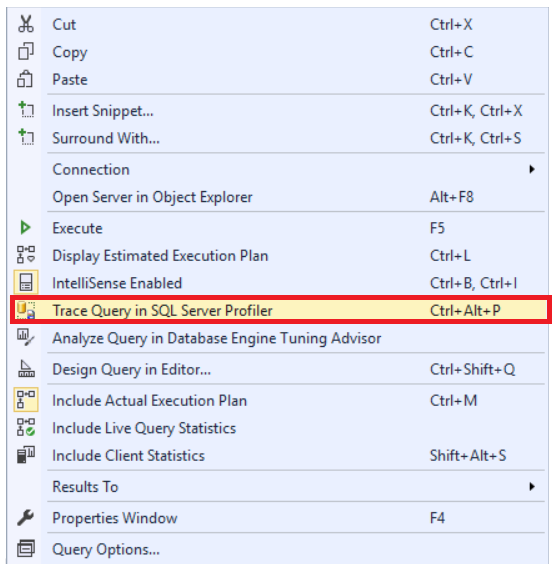
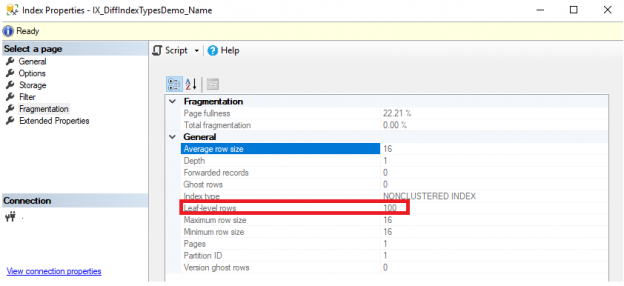
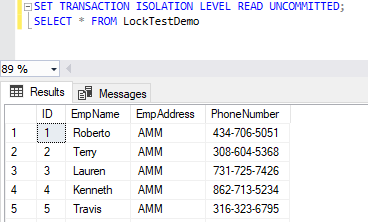
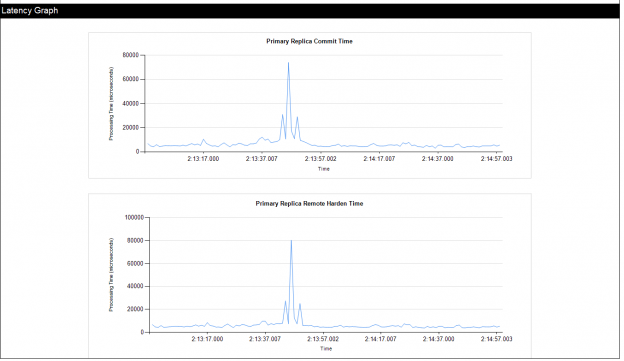
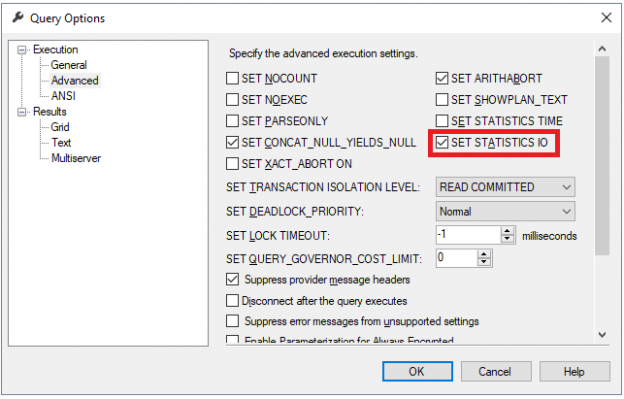
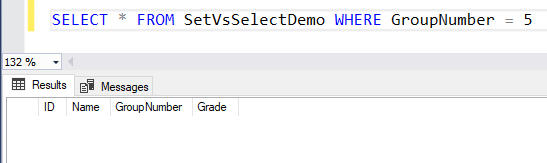
SQL Server Management Studio aka SSMS is the default integrated graphical user interface tool that is used to access, administrate, configure, manage, query and monitor the different SQL Server instances that are hosted locally at the user machine, remotely on a server or anywhere in the cloud. It is a comprehensive environment that allows us to edit, debug and deploy scripts written in different languages such as T-SQL, DAX, MDX, XML and more.
In my previous articles, we followed the enhancements to the existing SSMS features, the fixes to the bugs found and reported in the previous SSMS versions and the new features added to each new release. These new features that are introduced in the previous versions include the Connections dialog box new options, the embedded Performance Dashboard, Showplan node search, Import Flat File Wizard, the XEvent Profiler and Always On Availability Group dashboard new additions, which are described deeply in these articles.
Read more »