This article will cover the SQL ORDER BY clause including syntax, usage scenarios to sort out results in a Select statement.
Read more »
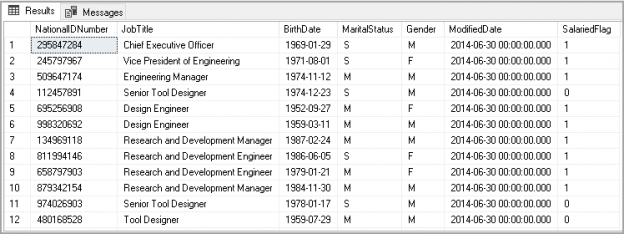


This article will cover the SQL ORDER BY clause including syntax, usage scenarios to sort out results in a Select statement.
Read more »
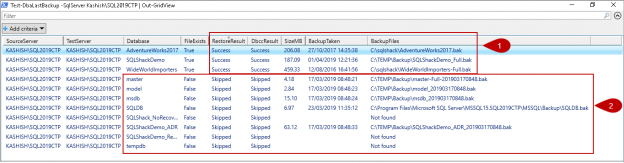
In this article, we will explore database backup validation by with SQL restore database operations using DBATools.
Read more »
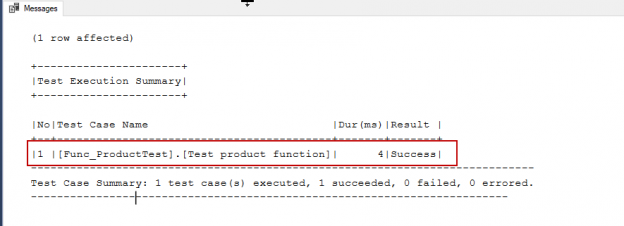
SQL unit testing is a testing method which allows us to test the smallest, atomic programmable part of a database object. SQL unit testing plays a key role in the modern database development cycle because it allows us to test individual parts of the database objects work as expected. SQL unit testing adds a great worth to the database project because unit tests are more reliable then manual test methods.
Read more »
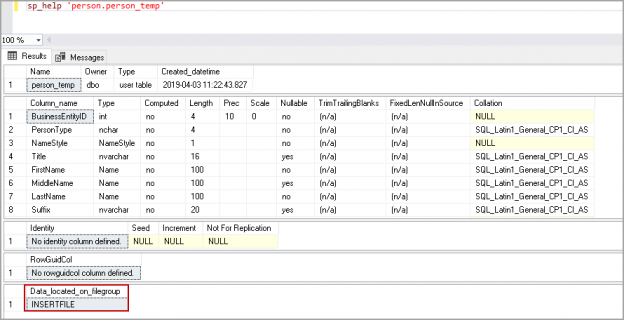
This article will cover the SQL SELECT INTO statement including syntax, parameters and use with multiple tables, filegroups and a WHERE condition
Read more »
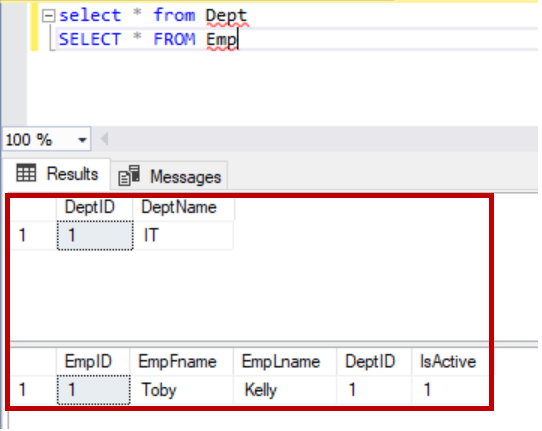
In this article let us review different ways to create a SQL foreign key, rules on updates and deletes, enabling foreign key constraints, disabling foreign key constraints and not for replication in foreign keys.
Read more »
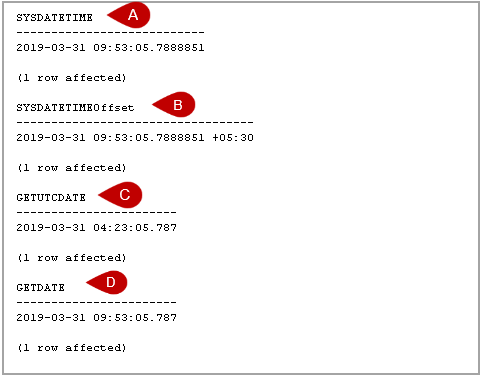
In this article, we will explore various SQL Convert Date formats to use in writing SQL queries.
Read more »
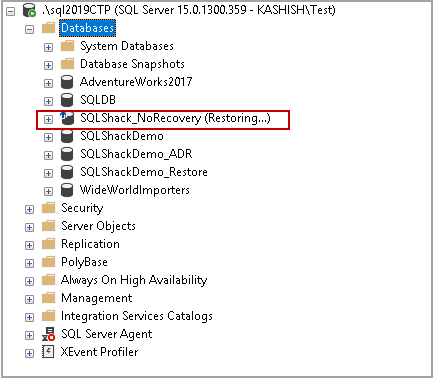
This article will cover SQL restore database operations using the open-source PowerShell module, DBAtools, and will cover commands for backup restoration using the command Restore-DBABackup with many various permutations like restoring from file, separate directory, renaming databases, norecovery options and more
Read more »
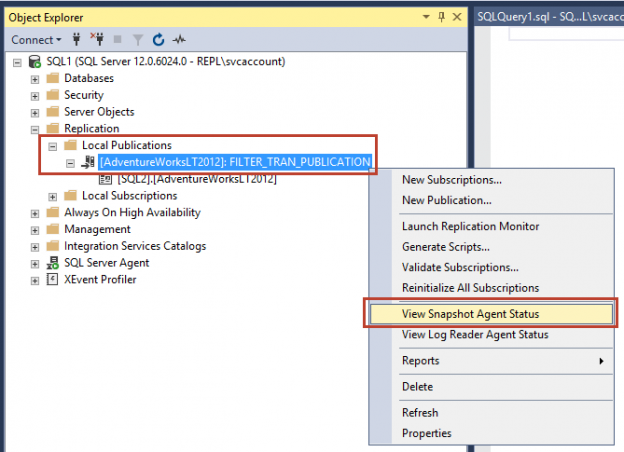
In the last articles, we have learned Configuring Snapshot and Transactional SQL Server replication and Configuring Peer to Peer and Merge SQL replication. Now, once we configured SQL Server replication, there will be some instances where we need to modify the SQL Server replication configuration as per the project updates. In this article, we will learn a few modifications in the existing SQL Replication such as Add new article, drop an article and change the Snapshot folder path and data filter in the current SQL Server replication.

A common task for newbies is to learn how to do a SQL convert date and work to convert them date to other data types or covert other data types to Date.
Read more »
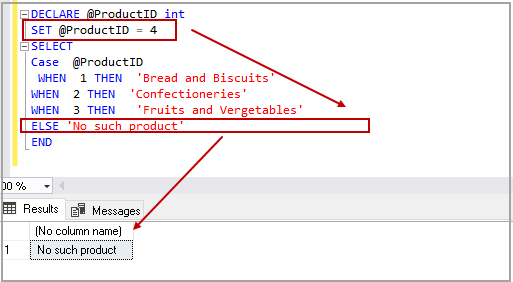
The case statement in SQL returns a value on a specified condition. We can use a Case statement in select queries along with Where, Order By, and Group By clause. It can be used in the Insert statement as well. In this article, we would explore the CASE statement and its various use cases.
Read more »
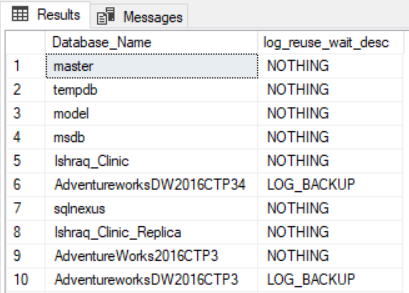
In the previous articles of this series on the SQL Server Transaction Log, we discussed the importance of the SQL Server Transaction Log and the role that it plays in maintaining the database consistency, by ensuring that the committing transactions data will be preserved and the failed transaction will be rolled back. It also helps to recover the database to a specific point in time in case of system or hardware failure. This is achieved by writing a log record to the SQL transaction log file before writing the data pages to the physical data file, using Write-ahead Logging process.
Read more »
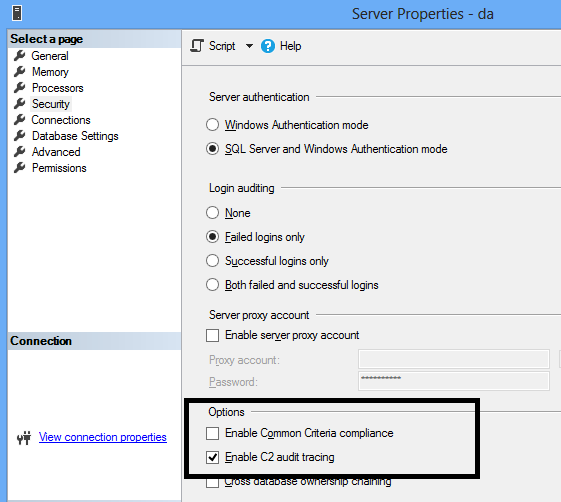
This article will cover SQL Server C2 auditing using C2 audit mode including an introduction, comparison of auditing technologies, configuration and common criteria compliance
Read more »
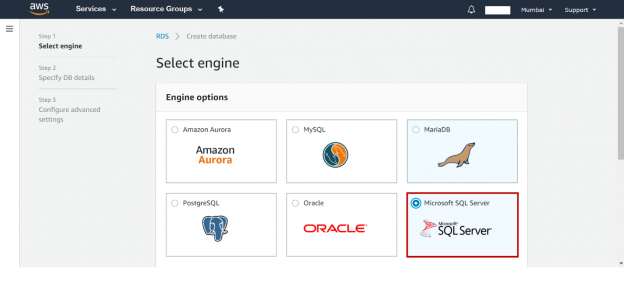
This article will review on how to launch an AWS RDS SQL Server instance and how to connect the instance and modify the properties of database instance.
Read more »
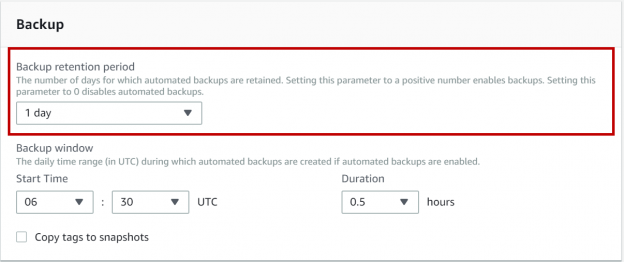
This article will review about the recovery models backups and restore options in available AWS RDS SQL Server.
Read more »
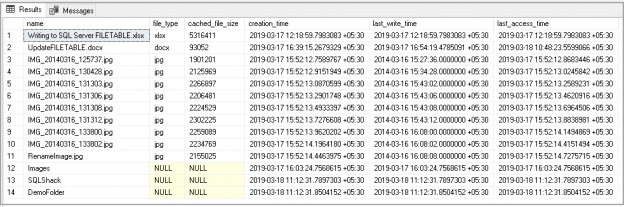
SQL Server FILETABLE provides benefits over SQL FILESTREAM available from SQL Server 2012. We can manage unstructured objects in the file system using SQL Server. It stores metadata in particular fixed schema tables and columns. It provides compatibility between an object in SQL Server table and Windows.
Read more »
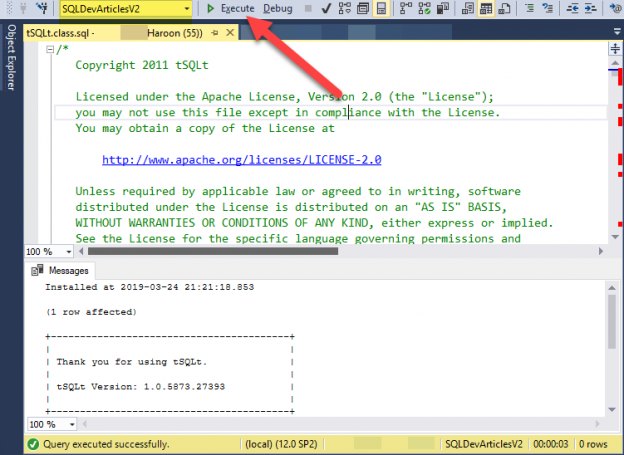
This article is about basics of conventional SQL unit testing concepts and its implementation through tSQLt, a highly acclaimed SQL unit testing framework because of being written in T-SQL and its built-in design support for SQL SQL unit testing needs ranging from simple to complex scenarios.

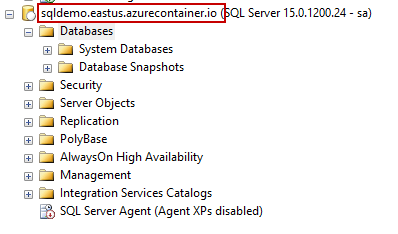
This guide is all about provisioning SQL Server 2019 using Azure Container Instance (ACI), including the installation and configuration. In this article, we talk about the Azure Container Instance (ACI), the Azure PowerShell module, installation and configuration of SQL Server using the Azure PowerShell module, and automation of installation and deployment using templates.
Read more »
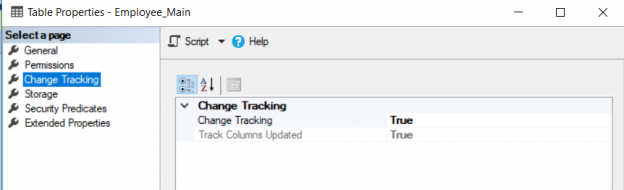
This continuation of our SQL Server auditing series is on SQL Server Change Tracking and will cover an overview, enabling, disabling, auditing DML changes including SQL updates and deletes.
Read more »
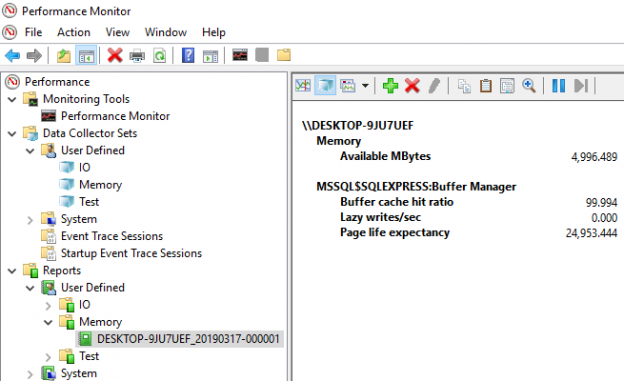
This article is the sequel in a series about SQL Server monitoring tools and common performance issues. The first article SQL Server monitoring tools for disk I/O performance is about how to detect and solve high input/output on hard disk subsystems when doing too much work during peak or maintenance times.

Nested Triggers in SQL Server are actions that automatically execute when a certain database operation is performed, for example, INSERT, DROP, UPDATE etc.
Read more »
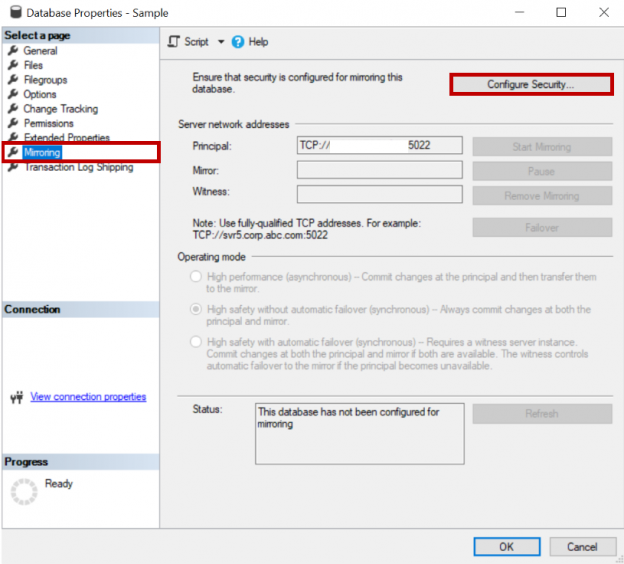
Both log shipping and mirroring are high availability and disaster recovery options available in SQL Server. This article will review on how to configure log shipping on a mirrored database.
Read more »
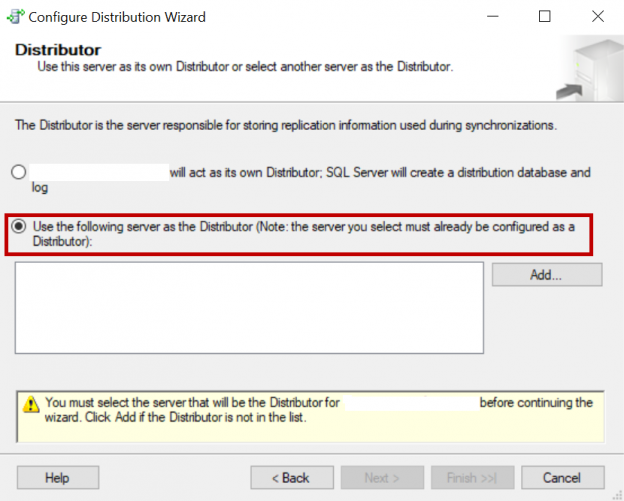
This article will review on how to configure SQL Server Replication along with mirroring on a database.

We have a convenient tool for working with PowerShell and SQL Server when using Invoke-SqlCmd. As we saw when running statements, we can run DDL and DML changes with the command without writing our own custom scripts. This carries advantages when we need to quickly develop with PowerShell, but it can come with drawbacks on security if we’re not careful how we use this function. We’ll look at security when using this function by starting with a few examples of what we can do when we have unlimited access along with how we can design to limit our environment to be strict with our use of this tool.
Read more »
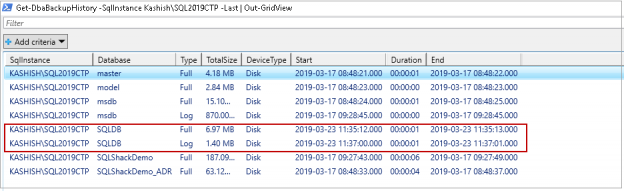
In my earlier PowerShell SQL Server article, SQL Database Backups using PowerShell Module – DBATools, we explored the importance of a disaster recovery solution for an organization. Microsoft offers various disaster recovery solutions in SQL Server.
Read more »
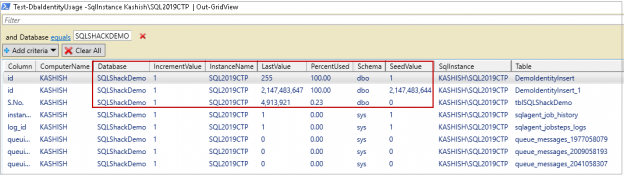
In this article, we will review PowerShell SQL Server module DBATools to identify IDENTITY columns about to reach the threshold.
Read more »© Quest Software Inc. ALL RIGHTS RESERVED. | GDPR | Terms of Use | Privacy