In this article, we will explain what the SQL injection attack is, why it could be hazardous, and how to defend our SQL database from this attack using parameterized queries and some third-party tools.
Read more »
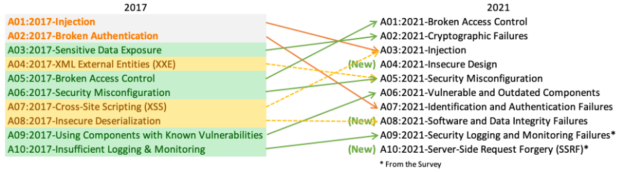


In this article, we will explain what the SQL injection attack is, why it could be hazardous, and how to defend our SQL database from this attack using parameterized queries and some third-party tools.
Read more »
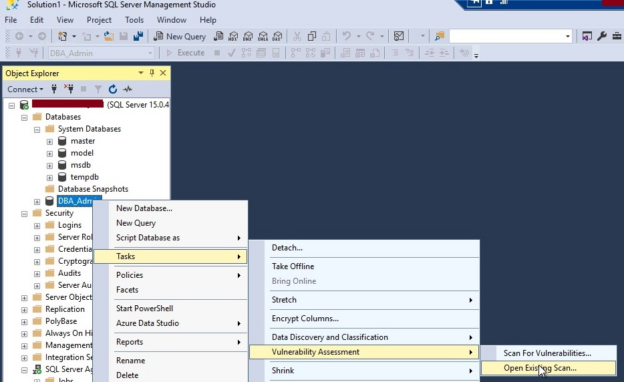
I will explain how to use and perform security testing using SQL Server vulnerability assessment in this article. I have explained basic understanding about multiple layers of security that we configure to protect our SQL Server instances in my last article. I have also explained about security testing at each layer we should perform to understand how secure our systems are. I would request you to read this article, Understanding security testing for SQL Server environments to learn more about them.
Read more »
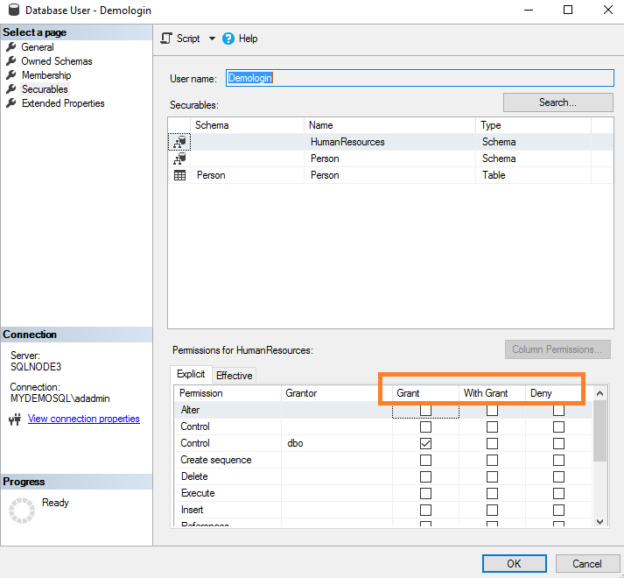
This article will walk you through Grant, With Grant, Revoke and Deny statements for both on-premises and Azure SQL Database.
Read more »
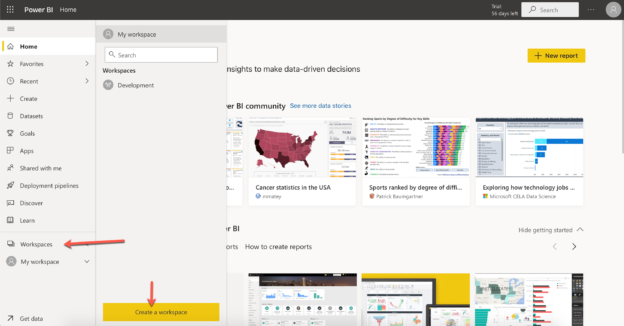
In this article, we are going to learn about implementing and managing security in Power BI Workspaces. Power BI is one of the leading data visualization tools that is used by a plethora of companies around the globe. Power BI has risen to prominence in recent years due to the ease of use and familiarity of concepts with Microsoft Excel, which helped a lot of analysts tutor themselves and learn to work in Power BI. Power BI is now available in both, desktop and the cloud and users can choose to start with anyone. However, the desktop version of Power BI, known as the Power BI Desktop is used mainly for creating simple and complex data models within the Power BI environment and then published to the cloud, known as the Power BI Service.
Read more »
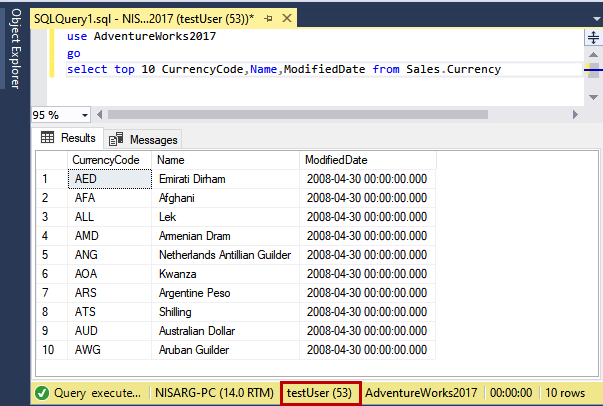
In this article, we are going to learn about the db_datareader role. It is a fixed, database-level role. The database-level roles are a group of security principals that are used to manage the permissions within the databases more efficiently. There are two types of database-level roles. One is a predefined database-level role, and another is custom database-level roles. The custom database-level roles can be created by the database administrator or the member of the db_owner role.
Read more »
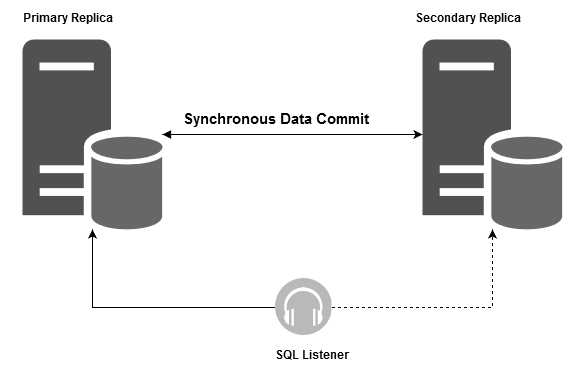
It is the 30th article in the SQL Server Always On Availability Groups series and explores column-level SQL Server encryption with AG groups.
Read more »
As tracking behavioral data becomes increasingly popular, firms may overlook areas where they can collect the same information while data masking details that can be used in a compromise. Behavioral data collection can be extremely dangerous as it allows attackers a wide range of attacks, from spoofing targets to automating custom attacks on targets. Since behavior can reveal key details about us, this information may be as costly as private identifiable information. When tracking behavioral data, we want to weigh risks, and, in some cases, we can accomplish the same result without specific details. In other cases, we may want to mask specific behavioral information on reports that are generated, even if we retain the specific time. We’ll look at a method where we can accomplish either – updating data to remove time or data masking specific time while returning the information we want.
Read more »

When we develop security testing within inconsistent data volume situations, we should consider our use of anti-malware applications that use behavioral analysis. Many of these applications are designed to catch and flag unusual behavior. This may help prevent attacks, but it may also cause ETL flows to be disrupted, potentially disrupting our customers or clients. While we may have a consistent flow of data throughout a time period – allowing for a normal window of behavior to occur – we may also have an inconsistent data schedule or inconsistent amount of data that cause these applications to flag files, directories, or the process itself.
Read more »
When we create an environment and consider our security testing from development to production and how changes are deployed throughout each environment, we want to consider what we’re protecting and how much resources we’ll devote to this protection. Every company has limited resources, so protecting against all possible threats will not be something we can achieve.
Read more »
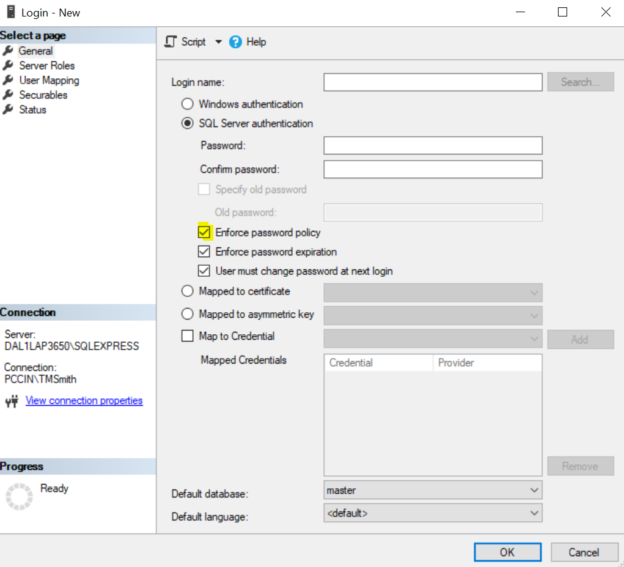
In this article, we’ll look at using the built-in PWDCOMPARE function in SQL Server for security testing passwords. While this tool may seem like it exposes a weakness in Microsoft SQL Server because we can test for passwords, it should be of note that an attacker could do the same attack by attempting to login to our database server assuming the attacker was able to access a connection to it. Therefore, this function does not increase the risk of an attack on SQL Server but does help us identify possible weaknesses in our environment so that we can quickly mitigate these risks. In addition, we’ll also combine this with other related tools in SQL Server to help us with logins.
Read more »
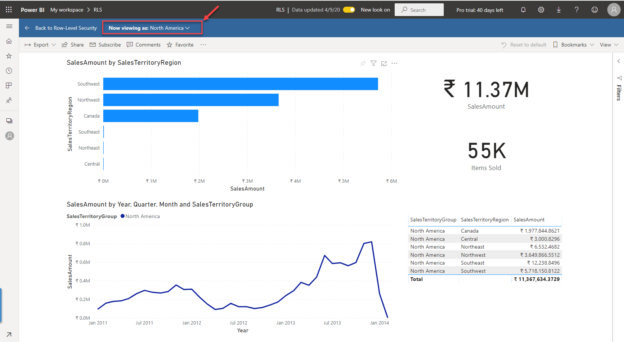
Analyzing data with Power BI has always been fascinating to me. With ever-growing data comes more risk, and hence more security is needed. In this article, I am going to introduce what row-level security in Power BI is and how does it work. I’ll also demonstrate in detail how to implement the same in Power BI Desktop. Later, we will also discuss how to implement this row-level security in Power BI service as well. To learn about row-level security in SQL Server, please have a look at my previous article, where I have explained how to implement the same.
Read more »
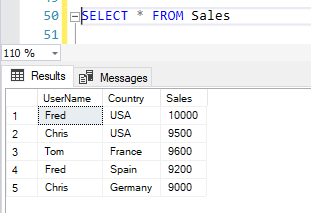
In this article, I’m going to discuss Row-Level Security in SQL Server. RLS or Row-Level Security as the name suggests is a security mechanism that restricts the records from a SQL Server table based on the authorization context of the current user that is logged in. This means the records from the tables are displayed based on who the user is and to which records do the user has access to. This is usually done to allow specific users to have access to their data only without permission to view other users’ data.
Read more »
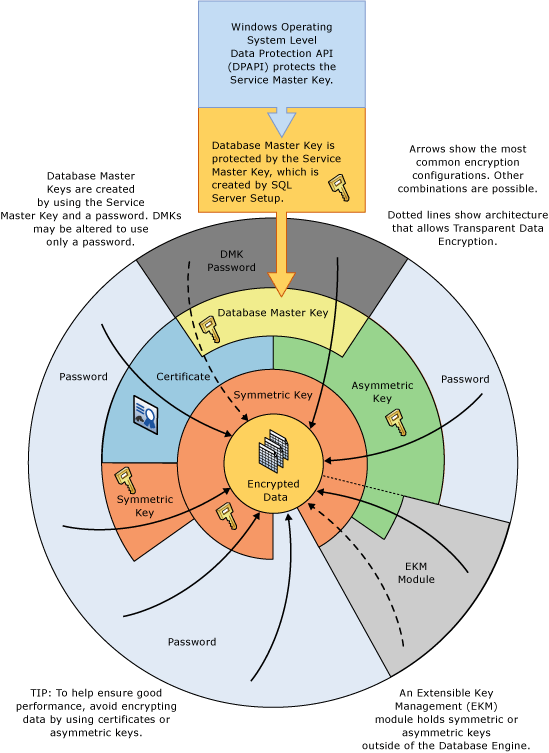
This article gives an overview of column level SQL Server encryption using examples.
Read more »
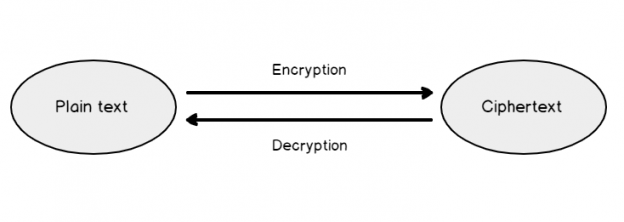
This article explores the Python scripts for encrypting and decrypting passwords in SQL Server using Azure Data Studio SQL Notebooks.
Read more »
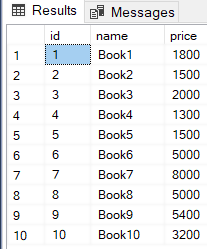
A SQL injection attack is one of the most commonly used hacking techniques. It allows hacks to access information from a database that is otherwise not publically accessible.
Read more »
Security has been one of the prime concerns of database developers since the inception of database management systems. Various data protection schemes have been introduced to provide secure access to sensitive data.
Read more »
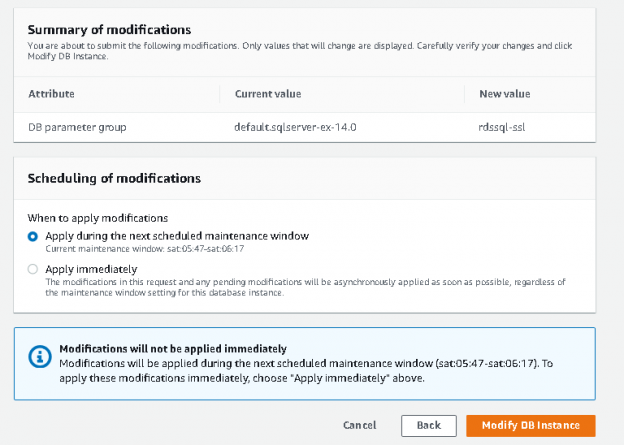
This article explores a method to enforce SSL for all connections in AWS RDS SQL Server.
Read more »
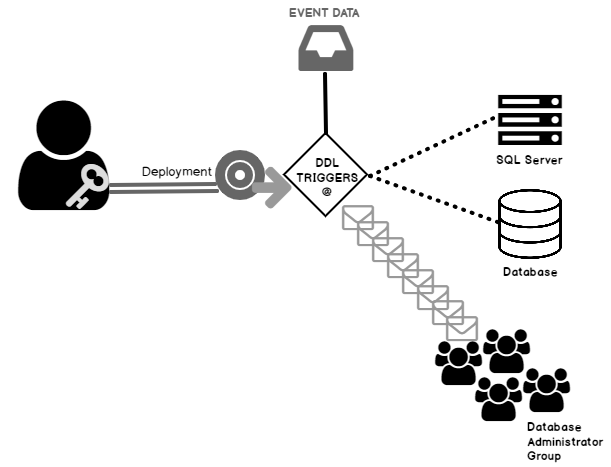
In this article, we will un-riddle the ways to make use of the data definition language trigger (DDL Trigger), in order to monitor the progressions made to the database programming objects, View, Procedure or Function with a few real-time examples.
Read more »
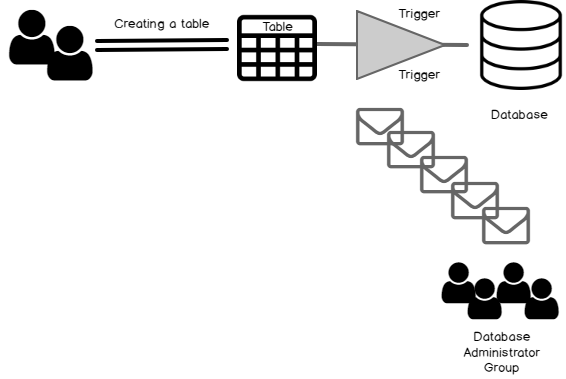
This article portrays the different utilization of database DDL Triggers for the Tables with a counting mail alert on schema composition using DDL (Data Definition Language) standard. Using that efficient method we can keep close eyes on monitoring schema changes in any database of SQL Server. We’ll also see how we could monitor these movements and send an alert email to persons responsible to inform about this change.
Read more »
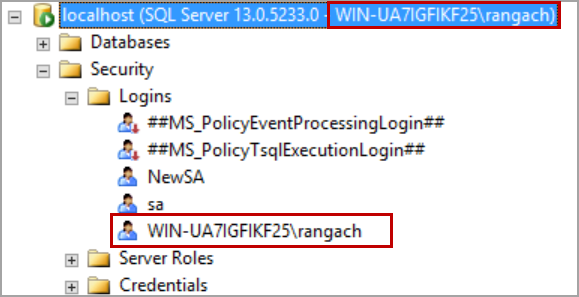
In this article, we will review how to recover SA password by starting SQL Server in single user mode when you forget “sa” credentials or lose the access to the instances due to the following reasons:
Read more »
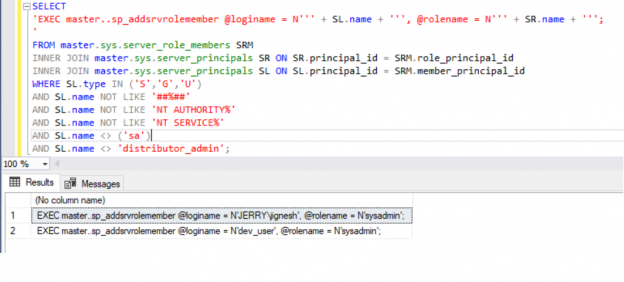
This article speaks to, how to copy SQL Logins on the new server with Server Level roles and database-level permissions as existing Source to Destination SQL Server instance using a script.
Read more »
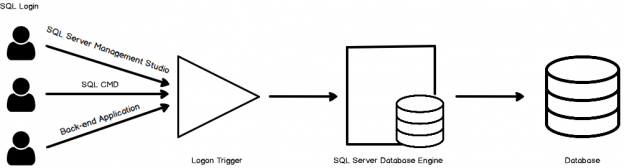
This article contains the SQL Server login Authentication scope on the Security side. We will find the subtleties, how Login Authentication extension can be controlled SQL Server level Logon trigger.
Read more »
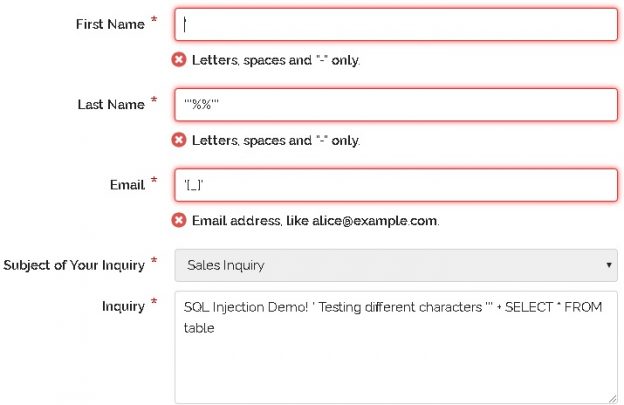
With an understanding of what SQL injection is and why it is important to an organization, we can shift into a discussion of how to prevent it. We ultimately want systems where SQL injection is impossible or very difficult to pull off. We then want systems where exploiting bugs is slow, laborious, and likely to raise monitoring alarms within an organization when attempted. The trio of layered security, prevention, and alerting can provide an immense advantage against not only SQL injection, but other data security threats.
Read more »
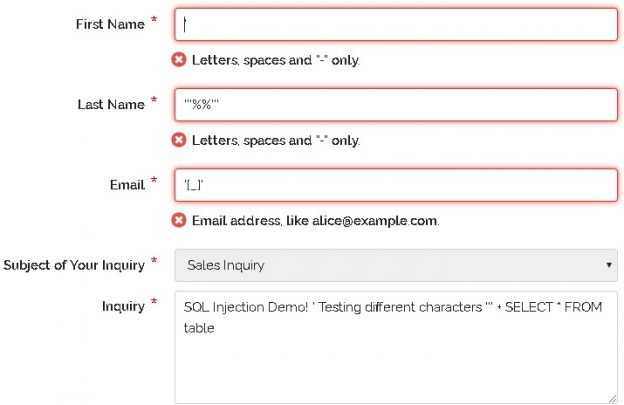
Many security vulnerabilities are discovered, patched, and go away forever. Some linger and continue to plague software development and will continue to do so for years to come. Setting aside social engineering and non-technical attacks, SQL injection remains one of the top security threats to our data, as well as one of the most misunderstood.
Read more »
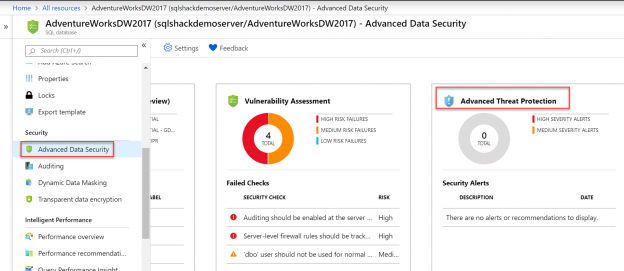
In today’s time where data breaches are highly expected to happen, there is a high need to ensure sensitive data in the Azure SQL databases is secured and which is why data security implementation is gaining momentum across each community. We covered one of the features of Advanced Data Security here in Advanced Data Security in Azure SQL Database – Data Discovery & Classification. Let’s dive further into the other two features that Azure SQL offers with this capability in this article.
Read more »© Quest Software Inc. ALL RIGHTS RESERVED. | GDPR | Terms of Use | Privacy