This article will explain various aspects of security testing for the SQL Server environment. Security is a very critical area for any database environment. We must properly plan, deploy, and audit database security measures to protect and prevent any unauthorized access of the data. We should also perform regular security testing to ensure we have the right set of rules and policies in place to secure our database environment. Database security measures also help any organization to protect its data to maintain its privacy and integrity.
Security testing is a process through which we try to compromise various security measures of applications, databases, or systems. It is also a process of developing or creating test cases that can destabilize a system’s security checks. Let’s first understand all security measures we apply at various layers of the running systems in the SQL Server environment.
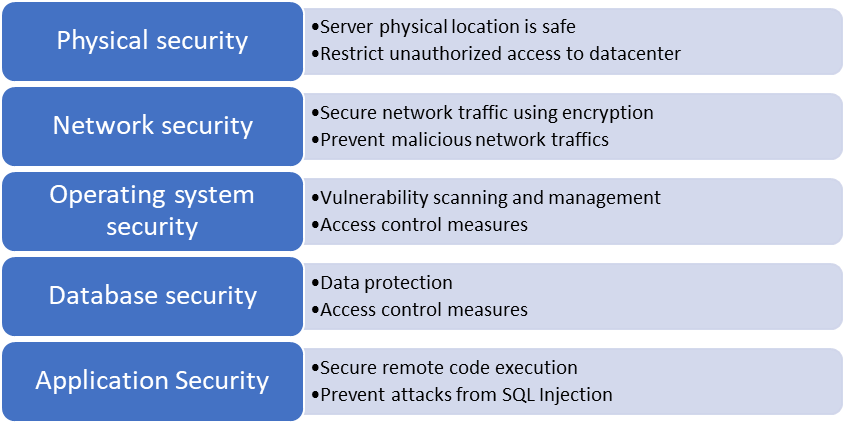
Security Layers for SQL Server
We can categorize SQL Server security into various layers to secure and protect its instances and databases and for easy manageability. These layers could be:
- Physical security
- Network security
- Operating system security
- Database security
- Application security
The below picture is giving high-level objectives of each layer given above.
Physical security for databases systems is moreover about securing the servers and all related network and hardware devices hosted in your data center. You can restrict people to access your data center premises where you have physically hosted these systems. Make sure to configure a copy of backups for all critical systems to another location to protect your data in case something happens to this site. Ensure to have auditing in place about who all are visiting this place and for which reason. You can audit who all have access to this location, make sure to have a proper approval process in place if somebody needs to be granted access to data center premises. Install CCTV cameras to monitor the security of the building. We try to compromise all these rules and policies during its security testing.
If you have hosted all your systems in a cloud environment, then you should rely on your cloud providers as all cloud providers follow best practices to secure their data centers.
Next comes Network security where we ensure that all communications are safe and secure. We also ensure that malicious network traffic is not being targeted using bots or any programs or by any means to our systems to make them degraded or inaccessible. The objective of the network security layer is to make sure:
- All unwanted ports are blocked
- Firewall policies are in place to prevent malicious external network traffic
- All network endpoints are protected by any means like encryption or third-party tools
- All packets which are coming in or going out of the systems are encrypted
- Fix all vulnerabilities identified on any network component or software to minimize the security risks, they can compromise the system to external threats
Operating system security involves security at the platform level and prevents any unauthorized access to the database system. Operating system security
- improves access management security by adopting complex password policies and multi-factor authentication
- secures systems with the help of firewalls to restrict unwanted system calls
- includes securing SQL Server binaries or any system or application files stored on the machine
- covers vulnerabilities scanning and apply updates to fix operating system and SQL Server security risks
- Restrict unwanted services by limiting the surface area of SQL Server
The next one is Database security where we secure databases and their objects at various levels by adopting adequate access control measures inside the database system. We can divide the database security into the below 4 categories.
- Authentication
- Authorization
- Data protection
- SQL Server configurations
Authentication is the first step to connecting to the databases. It is a process to recognize that some authentic person is using a valid principal or login to connect to the database. If you are using an invalid principal, then we can say your authentication is failed and you cannot connect to the database.
Below are the few points you must consider while allowing somebody to authenticate your systems:
- Make sure to define password policy to choose complex passwords and change the passwords at some intervals
- Assign all users to use multi-factor authentication wherever it is possible
- Grant only required permissions and restrict any unwanted higher privileges
- Do not allow anybody to use generic accounts like sa in SQL Server. Remove or disable them.
Authorization is a process to grant access to objects. You can restrict or authorize somebody on his principal to access that database object. Even you can control the type of access like if you don’t want them to write or update anything in the database object then you can do that by denying these rights on that specified object.
Data protection is the third option that is very popular these days to protect data using encryption from unauthorized use. It is used to encrypt our data at rest or on transit for SQL Server databases. SQL Server offers multiple options to apply encryption or masking for various types of needs like Transparent Data Encryption, Always Encryption, Data Masking, etc. Database backups can also be encrypted to prevent any unauthorized access of its data.
The last option is to carefully configure your SQL Server instance so that none of your data can be compromised using either way. We must consider changing SQL Server default port to other port, disable unwanted SQL server services like SQL browser service, we can disable some system objects like xp_cmdshell, etc., remove generic accounts, etc.
Application security is the final layer where we need to apply all possible measures to establish a secure connection to the database server prevent unauthorized remote code executions. The SQL Injection attacks are also categorized and taken care of at this layer to prevent any malicious code to be inserted into your application program and execute them on the database to corrupt the data.
There are various third-party tools in the market that you can use to configure the above security measures.
Now, we have understood all security measures and policies we should adopt to protect the database environment. Next, we will learn about security testing through which we try to compromise our systems and databases to understand weaknesses present in the systems.
Security testing in SQL Server
The above section has explained the basics about security measures at various layers we can take to secure our databases and systems on which they are hosted. Once you apply those measures and procedures, you must also test them from time to time to ensure everything is in place and working fine as per our expectations.
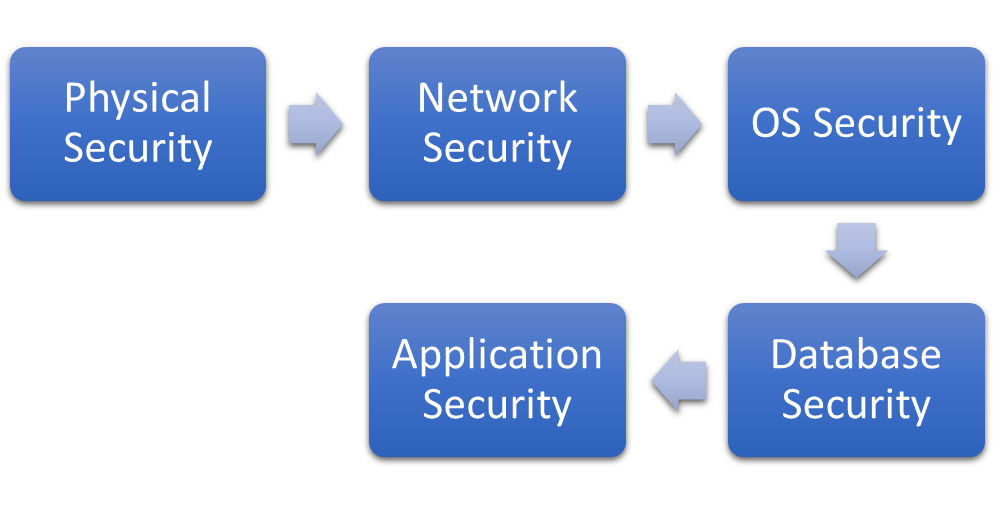
The security testing for any system helps us to identify possible security holes and vulnerabilities present in the system and allows us to fix them on time by applying appropriate remediations to protect databases and their systems from any internal or external security threats. It also helps to maintain the availability of SLA of the databases by detecting the risks and remediating them on time. If you are confused about where to start, then you can follow same sequence which is showing in the below image. You can start with testing physical security and follow the same order till Application security testing to ensure end to end security of your database system.
Also, remember security testing exercise is a time-consuming process that can cost you more in terms of efforts and additional dollar values. Like we apply various security measures at multiple layers as defined in the above section, similarly, we should perform its testing at each layer wherever we have implemented our policies to secure the environment. These layers are the same as they are defined in the above section.
- Physical security
- Network security
- Operating system security
- Database security
- Application security
Physical security testing can be taken care of by frequent audits and proper checklist-based documentations. Ensure to properly lock premises where systems are hosted. Make sure to follow all best practices to maintain physical security to safeguard from fire, flood, theft, or any man-made tragedies.
As part of its testing, you can plan the below steps:
- Attempt to enter the data center room without having any access or you can try tailgate to enter the room
- Perform mock drills to secure the building from fire, earthquakes, or manmade accidents
- Attempt to bypass security barrier to ensure all security personnel are attentive or not
- Try to compromise cameras installed to monitor all the activities for the data center
Gather details during each attempt and analyze whether best practices or defined policies have been followed during test cases or not. If you find any miss, then you can take additional measures to make sure it could be followed next time.
Network security testing involves port scanning to identify any devices that are connected and accepting only secure connections, detect any port that is left open, vulnerability scanning to detect any security risk that can lead to external expose of the system, weak passwords auditing, and identifying wherever multi-factor authentication is not configured, and penetration testing to identify existing security vulnerabilities.
You can perform all these testing using various tools like Qualys, Acunetix, NMAP, Wireshark, etc. The main points which we must cover during this testing are:
- Perform vulnerability scanning and identify any loophole which can be used to compromise your devices
- Scan all ports to identify which port can be compromised
- Penetration testing
- Access control auditing
Ensure to take remediations of all risks or loopholes identified during the above security testing.
Operating system security testing involves security and vulnerability scanning of the system, intruder detection testing, configurational and policies check to test, and security audits on access control management.
Testing comes under this layer is:
- Vulnerability scanning and risk assessment
- Attempt to compromise system using any configurational settings to ensure such settings and policies have been addressed
- Intruder detection testing to ensure unauthorized access cannot be made
- Weak password cracking
-
Try to use generic accounts, this will expose us to remove all generic accounts from the system
Database security testing also involves the same actions that we discussed for operating systems. It also involves access control management to review database authentication or authorization configurations, data is protected using encryption or not, unwanted features are not installed along with unwanted services should be disabled to reduce the surface area for attackers.
- Attempt to establish connections to the database instance or databases by various tools, other logins present in the system like service accounts, using generic accounts like sa, port numbers or by compromising weak passwords
- Attempt to access database objects which should be restricted for other users to ensure data theft is possible or not
- Audit access management to make sure nobody has unnecessary higher privileges and unused logins
- Attempt to access data that is encrypted
- Make sure SQL Server has not been installed with unnecessary components
Apply fixes for identified weaknesses of the system during the above security testing to secure your systems.
Application security testing ensures secure connections to the database system to prevent attacks through SQL Injections. We can use third-party tools like SQLMap or SQLNinja to perform this testing. These tools will help us to identify weaknesses that an external attacker can use to inject malicious SQL codes in system calls (SQL Injections) at the application security layer.
We can test the below points in this layer of testing to prevent SQL Injection attacks.
- Attempt to compromise remote execution calls
- Try to insert malicious SQL statements to corrupt your data
Take corrective measures to fix weaknesses identified during this security testing.
SQL Server has also introduced a feature called Vulnerability Assessment which can be leveraged to identify all existing loopholes from SQL Server databases. This feature helps us to address database security layers and not the remaining other layers. You must engage all respective teams to look into their respective area to perform similar testing to make sure you have robust security measures in place to secure your database systems. You can also use SQL Server Policy-based management to identify and fix a specific security-related configuration item.
SQL Server also provides various catalog views, functions, and dynamic management views and functions using which we can perform audits or reviews of the existing security-related settings.
Conclusion
Security testing should be done regularly to ensure we are not deviating from our strict security policies. SQL Server offers various tools and utilities using which we can detect SQL Server database-level security risks and accordingly we can apply their fix. I will explain such tools, utilities, and system objects in my upcoming articles. Stay tuned for my next article in which I will explain one of such tools SQL Server Vulnerability Assessment in a step-by-step process on how to use it to detect and fix the existing vulnerabilities.
- Configure backup storage redundancy for Azure Cosmos DB account - May 15, 2024
- Difference between SQL SELECT UNIQUE and SELECT DISTINCT - January 16, 2024
- How to do a group by clause - April 12, 2023